Use SSH for more secure browsing in public networks
Posted on Wed 20 April 2011 in Security
In the time of free wifi and free internet connections in every hotel, bar or cafe you should be sure your connections are secure. In some cases you can't trust the connection but you need to go online and read some mails or share some documents. In this case some basic tools like SSH and Firefox can help you to build an secure connection to an known computer in the internet you can trust (for example your own root server).
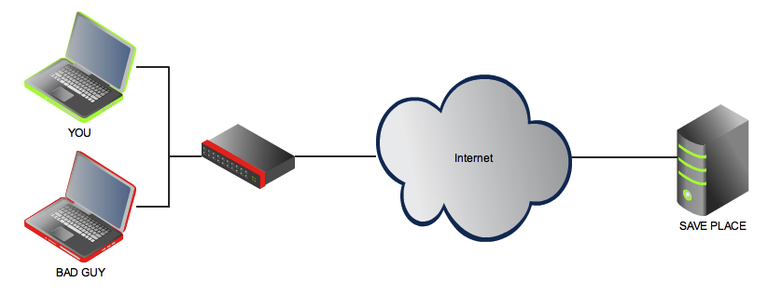
To make more clear what I am talking about i created this small diagram to make it more easy for me to explain what I am doing with this SSH connection and how I can benefit from it.
Let's say I am connected with an public network or wifi access point. There are many people around me using the same connection and I don't know the provider of the network very well. What I can do to get an secure connection is to open an SSH tunnel to my known machine and send all the traffic I am generating with my web browser through this tunnel.
This can be done with a SSH command like this:
ssh -D 8080 username@host
What this command does is explained in the man pages of the ssh command:
-D [bind_address:]portSpecifies a local ``dynamic'' application-level port forwarding. This works by allocating asocket to listen to port on the local side, optionally bound to the specified bind_address.Whenever a connection is made to this port, the connection is forwarded over the secure chan-nel, and the application protocol is then used to determine where to connect to from the remotemachine. Currently the SOCKS4 and SOCKS5 protocols are supported, and ssh will act as a SOCKSserver. Only root can forward privileged ports. Dynamic port forwardings can also be speci-fied in the configuration file.IPv6 addresses can be specified with an alternative syntax: [bind_address/]port or by enclosingthe address in square brackets. Only the superuser can forward privileged ports. By default,the local port is bound in accordance with the GatewayPorts setting. However, an explicitbind_address may be used to bind the connection to a specific address. The bind_address of``localhost'' indicates that the listening port be bound for local use only, while an emptyaddress or `*' indicates that the port should be available from all interfaces.
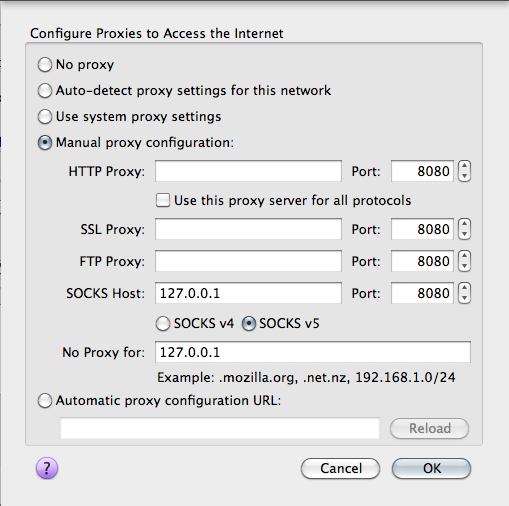
Now I have a local port (8080) where I can send my traffic trough. Only one thing I need to do now is to reconfigure my Firefox to use this port and connection and be sure DNS requests are sent through this secure connection as well.
Open the about:config page and set the following boolean.
If you want a possibility to activate and deactivate this proxy configuration with one click there are several firefox addons for managing proxy configurations like QuickProxy or FoxyProxy.
Another method of securing your browsing is the usage of the Tor network. Tor is a good and well known solution to protect your privacy.
If you are more familiar with server administration you should setup an own vpn server for you.
One big advantage of the usage of an VPN solution is that you can tunnel your complete traffic no matter from what application to a trusted endpoint and from there to the internet. This is the best solution if you really don't trust the network and you need to go online with you mail programm, your messenger or your custom application which does not use a encrypted or weak encryption mechanism.